Table of Contents
1. Antivirus
Check that you have antivirus.
In Windows > Search “Antivirus” > Click Virus & Threat Protection. The follow page will give you information on your antivirus and confirm that it is turned on.
Make sure it isn’t expired. Make sure it is from a reputable company. Make sure it is on. Make sure it scans automatically.
2. Firewall
In Windows > Search “Firewall” > Click Firewall & network protection. The follow page will give you information on your firewall is on in the domain, private, and public networks. If these are turned off, you may have a physical firewall present in different locations. This question may be geared toward an IT person who handles these things as there are many ways the Windows Firewall can be turned off, but the physical firewall is handling the load. In a normal scenario, if you don’t know – then you don’t.
3. Backup
Backup is different than Storage. Many people think Dropbox, Google Drive, Sharepoint, etc are backups, when they are really storage locations. Imagine that every file in Dropbox got encrypted or deleted or an ex employee emptied old data you didn’t notice until it was too late. Where do you turn for BACKUPS? Popular backup services include LiveDrive, Carbonite, iDrive, Backblaze, Acronis, SpiderOak One, Zoolz.
Be sure to know whether these are file backups, or full image backups.
File backups, as the name implies would restore the files on your computer, but not the software itself. These would be PDF’s, 1040’s, 1120’s, Excel sheets, and things of that nature. This type of backup is limited in that if you had Quickbooks Desktop, Tax Act, Drake, etc installed locally on your computer, you wouldn’t be able to restore with a file backup. The advantages are they are faster and usually contain what an accountant is looking for when doing a recovery.
Image backups are essentially a snapshot of exactly what the computer looked like at the time of backup. These not only include individual files, but operating system files, and programs as well. These restorations can take longer and use up more space, so they tend to cost more to maintain as well. When there is a specific line of business software that is manually installed on a computer or server, these are good options.
4. On Site Backup
On Site Backup comes in varying forms. A very simple form of on site back up would be moving files to a thumb drive. While this isn’t recommended and a manual process that often gets forgotten, it does count as “something.” However, if you end up needing to do a restoration from a thumb drive, then discover that you hadn’t done a backup in 4 months, you won’t feel that much relief missing the last few months.
A little better version would be the external hard drive and setting up some sort of automated backup software. You will need to be sure that these backups are tested. In the same scenario as above, you don’t want to find out your backups have issues when you need them. You want to discover and remediate before the problem happens. This is where having someone who looks over these things for you is very important.
If your IT person (or if you) set up a NAS, this would be an example of an on site backup. These are much faster when it comes to restoration as you are moving files via direct connection USB wire vs internet which can take a very long time to download and upload. The major disadvantage to on site backup is that if there is a fire or flood and you lose your data, the backup will most likely also be lost in the same accident.
This is why it is recommended to have both cloud and on site backups running so no matter the disaster that occurs, you have some form of recovery and don’t lose your business entirely.
5. Windows Patch Management
Type “updates” into the search bar and click Check for updates. The next screen will tell you the last time it was checked and if you have an organization who is responsible for it. If you do not see “Some settings are managed by your organization” then it is YOUR responsibility to keep these up to date.
Patch management is checking to see if your computer has all vulnerabilities plugged. Every 2nd Tuesday of the month, Microsoft releases big patches that should be applied as soon as possible. These patches can interfere with local software, so it is always important to test updates before doing a large deployment. Imagine if your firm had 50 employees, all using QB Desktop, and Microsoft releases a patch that causes QB Desktop to crash. All employees are scrambling to get any work done, and the only remedy is a long system restore.
The same is true with not applying the patches at all. In this scenario, there is a Windows vulnerability that has been detected and fixed, but your computer hasn’t applied the fix yet. Hackers gain access to the computer, and steal your clients’ information while everything looks fine on the surface. Then dealing with a data breach is a whole other can of worms.
Windows automatic updates are different than patch management. Windows installs small updates, but does not install the large important updates. This is why you need either a managed service provider handling them or a separate software.
6. 3rd Party Patch Management
3rd Party Patch Management, similar to Windows patch management is what software or organization is responsible for maintaining the updates on the programs on your system that aren’t Windows. There are plenty of times where you have seen things like update Java, update Adobe Reader, etc. This is how you manage to update all of those programs – even when there isn’t a notification.
A managed service provider (MSP) can handle these using remote monitoring software, or a user can try to do it themselves using programs like Ninite and Chocolatey. They do require some initial set up, but a lot of times can be handled internally. Having a monitoring software is important for these because trying to remember to check every single software on the computer manually for updates is grueling. It is important to update these because any software that is out of date is a potential for a hacker to get into the computer if not properly protected.
7. 2 Factor Authentication (2FA) or (MFA)
2FA many people have a love hate relationship with. The huge benefit is that if your password is stolen, the bad guys can’t get in without physically being next to your phone. The bad news is that every time you log in, you will need to be next to your phone.
This is a 1 second extra step, but pressing that one button can be the difference between losing everything and keeping a bad actor out. This is like a lock on the door at your house, most likely, when you leave someone won’t try to move the knob to get in, but if they did try, you want to make sure that it is locked and you need the key.
8. Drive Encryption
Drive Encryption is the status of the information on your physical hard drive. To paint a picture, if your laptop was stolen out of your car, anybody can get all of the information off of it by connecting it to another computer. The process is fairly simple and a $30 tool on Amazon can get the job done by even a novice.
They won’t need the password from the computer to be able to access the data, as it isn’t encrypted. Hence, drive encryption, forces that the data be decrypted on each login. This process happens in the background and has virtually no impact on performance. If the computer were stolen and connected to another device to try and steal the data, the hard drive wouldn’t show and the data wouldn’t be legible without the decryption key.
On a Windows Computer you can tell whether or not you have encryption enabled by clicking on This PC
If there is a lock logo – you have encryption. If it looks like the hard drive on the right with no lock, there isn’t encryption on the hard drive.
9. VPN
VPN – Virtual Private Network is a way to encrypting your network traffic.
In Windows open the Run Box and type in “ncpa.cpl”
When looking at this list of available connections you can tell if you have VPN set up and if it is functioning. In the below picture, VPN is cancelled and not working, but IS installed.
10. Written Data Security Plan
Any accountant with a PTIN needs to have a written data security plan. This outlines who is responsible for what and the strengths & weaknesses in your cyber security & client data protection. We have a comprehensive template you can download here
11. Complex Unique Passwords
Group policy in Windows professional can create rules for the organization on how complicated your passwords must be. If you are using a software like LastPass to manage your passwords, confirm that they are all unique and complicated. If you use the same password on multiple sites and one that isn’t important gets breached, that password and username combination is still available for hackers to use.
This is especially important for your accounting software that contains PII (personally identifiable information). You need to make sure that you are doing everything in your power to negate password hacking.
You can test your password strength here. Furthermore, you can see if a password you do frequently use is available check out this site. If you use a frequent password on a site that has been breached, make sure you change all of them ASAP.
12. Non-Identifying Wifi
Your public WiFi network name should not be something that identifies what information is hidden. For instance, instead of calling the wifi “ABC Accounting Firm” you should opt to more ambiguous names like “Ice Cream.”
In the bottom right corner of your screen you will see the a wifi logo or computer. You can hover over these icons to see what your network name is called and decide whether or not you need to change it. Do note that if you change your wifi name, a lot of devices may look for the old name and need to be reconfigured. This includes Alexa, computers, tablets, and many IoT devices.
13. Monitor EFIN / PTIN for Abuse?
As part of the ongoing concerns about security and identity theft, the IRS recommends that you verify the number of returns submitted under your EFIN. Do this routinely and especially during filing season. Verify your EFIN through IRS e-Services. If you do not have an e-Services account, then your first step would be to go to e-Services and register for an account.
Once you have logged into your e-Services account, follow these steps to verify the number of returns electronically filed with the IRS:
1. Select your name
2. In the left banner, select ‘Application’,
3. In the left banner, select ‘e-File Application’,
4. Select your name again,
5. In the listing, select ‘EFIN Status’ and on this screen you can see the number of returns filed based on return type.
14. Anti Phishing Toolbar
In the browser that you primary use for internet (Chrome, Edge, Firefox, etc). You can check in the upper right corner to see which plugins are actively running. There should be something that checks to see whether or not websites you visit are legitimate or phishing. These can appear in search engines with green checks verifying that websites are legitimate or you should be weary of.
15. Avoid Accessing Email On Public Wifi
This is a best practice, but very important. If you are on a laptop or tablet and traveling there will inevitably be times where you need to use a WiFi that isn’t your own. These can be at airports, coffee shops, etc. You need to make sure that you are connecting through a VPN in order to make sure that the data you transmit is encrypted. A threat actor could set up a WiFi network called “airport” that doesn’t have encryption, and many people will connect. This gives them access to see the emails you send and information you view online.
16. Portal For Clients To Upload Secure Documents
If your clients are emailing you attachments of their W-2’s, 1099’s, etc you are doing it wrong. Clients need to have a portal where they can safely upload documents and the accountant can view it, knowing that it is encrypted and safe from prying eyes. Some of the big players in this space are ShareFile, Encyro, and even Dropbox. Do not let clients send you PII through email, it isn’t safe!
17. No Default Passwords
Many network devices (routers, modems, etc) come with default credentials that you are supposed to change when the network is first set up. You can see if you fall into this by opening a command prompt (windows > cmd > )
Type “ipconfig” in the results you will see a line that says default gateway, usually followed by 192.168.1.1 or 10.1.10.1 (usually a variation of those numbers that tend to end in 1 or 254).
Type that number into your browser (Chrome, Firefox, Edge) and you should get a prompt to login to the network.
From there, you can Google the term “<network brand> default login” if those credentials that show up in Google get you into the network that means that you have default passwords on the system and anyone looking to get in can perform these as well. In the above example we are in ATT which has an automatic login and followed by an access code that is physically on the router. This code is needed to really do damage.
18. Auto Logoff Screensaver
Search in Windows for Screen Saver. Change the Wait to 15 minutes and check the on resume, display logon screen.
19. Security Awareness Training
Not clicking on the bad links in the first place is the best way to prevent data theft and being hacked. There are lots of resources for CPE in cyber security from places like the AICPA, and myCPE. You can also use a 3rd party like a managed service provider or a software like KnowBe4 to do constant testing.
20. Spam Filtering
92% of hacks originate from the email inbox. Having an extra layer of protection there can help prevent a majority of the issues that happen in an accounting firm. You can use configurations from a tech company that monitors or a third party software like ProofPoint or SpamTitant to handle these configurations and keep the bad guys out.
21. Remote Access Turned Off
Many people like using things like unattended access to be able to access their work computers from home. These are a gateway into bigger problems if the credentials get into the wrong hands.
Search “Remote Desktop Settings” and ensure that the Enable Remote Desktop is turned OFF
Only leave this open if it is has been configured from an IT professional and incorporates things like 2FA, VPN, and a very strong unique password. The same goes for if you have software installed like TeamViewer or AnyDesk that allow remote access from a different computer into the network. While they are convenient, it can open a gateway into a lot of problems down the road. If those credentials are compromised and someone gets onto a work computer, they can take everything without even leaving a trace of what happened.
22. Finding Computer Information
Or type “about” in the search bar at the bottom
23. Finding Anti Spyware Extensions
Click on the Hamburger
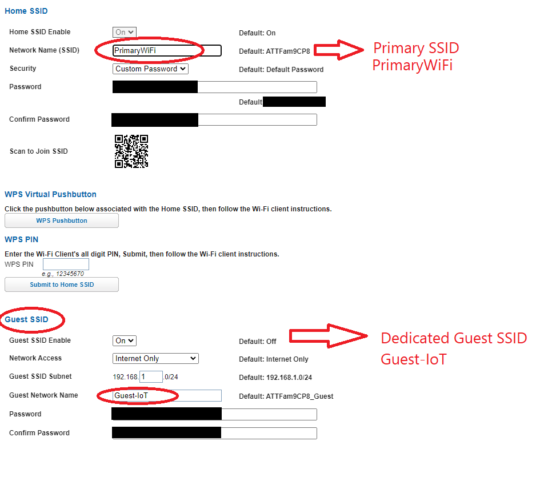
24. Dedicated IoT/Guest SSID?
To find the answer to this, you will need to look at your gateway provider and see if the guest network has been set up. There are hundreds of different brands so we can’t show all of the different examples, but below is a for instance on an AT&T ISP.
25. Is Group Policy Set Up To Enforce Password Complexity / Enforce Password Expiration?
Open the Run Box
Type “gpedit.msc”
* If you receive an error here, you most likely are using the Home edition of Windows and will need to purchase the Pro edition of Windows.
For solo practitioners without a domain / server / active directory Navigate:
Local Computer Policy > Computer Configuration > Windows Settings > Security Settings > Password Policy > view “Password must meet complexity requirements” and “Maximum password age”
If you are connected through a domain / server / active directory view the instructions here:
26. What is the IP Address of your server?
Open the run box and type > ncpa.cpl
You will see network connections. Double click on the one that your business runs off of.
In the status page, go to Properties
On the properties page double click on “Internet Protocol Version 4 (TCP/IPv4)
From this page you will see if you use a DNS to connect to a server or if the server address is automatic (meaning you aren’t using a server)
27. What method do you send encrypted documents?
There are lots of options of software that accomplishes this.
Some of the most popular are ShareFile, Encyro, Liscio, and SmartVault.